Table of Contents

According to a near recent Kaspersky report, over 98% of mobile malware targets Android devices. So, for Android app developers, prioritizing Android app security is paramount.
It ensures that user data remains safe and the app functions as intended. When developers prioritize security, they build trust with users, leading to higher adoption rates.
Basic Android app security measures like encrypting data by using SSL, and safeguarding code by using obfuscation and minification tools ensure it is difficult for anyone to steal sensitive data or reverse engineer and tamper with your code. And, implementing proper authentication protocols can shield your apps from common cyber threats.
The Challenges of Android App Security
Android is the world’s most popular mobile operating system, and with its vast ecosystem, there come numerous security challenges:
- Fragmentation: Android devices come in various versions with different hardware configurations. Many devices run outdated versions of the Android OS, which might not have the latest security patches.
- App Source: While the Google Play Store has a review process, Android’s open nature allows users to install apps from third-party stores or direct APK downloads. These sources might not be as thoroughly vetted for malicious software.
- Permissions Model: While recent versions of Android have improved app permissions, many apps still request more permissions than necessary. Users often grant these permissions without understanding the risks.
- Malware: Due to its open nature and popularity, Android is a significant target for malware. Apps can be embedded with malicious code, leading to data theft, unauthorized access, or other malicious activities.
- Insecure Code: Developers might not always follow best practices when building apps. Insecure coding can lead to vulnerabilities like SQL injection, exposure of sensitive data, or insecure communication.
If you adhere to security best practices, you can guarantee a smoother user experience and reduce the risks of app-related incidents. Remember that a secure app not only safeguards user data. It also protects your reputation as a developer, so, it is a win-win. Here is the best practices for Android App Security:
Android App Permissions
Android App Permissions play a crucial role in safeguarding your device and personal data. Granting only essential permissions ensures that apps have access only to what they truly need, reducing potential security risks.
Regularly reviewing app permissions is also wise, as updates may alter their requirements. If an app requests unnecessary access, it’s best to remove it altogether. Here are five Android app permission best practices you will want to adhere to for the best user experience and app performance;
Implementing Data Encryption
Implementing data encryption is the cornerstone of a solid Android app security plan. It ensures that sensitive information is converted into a code, making it unreadable to unauthorized parties.
This practice is crucial because it shields user data from potential breaches or unauthorized access. To implement data encryption, developers can utilize Android’s built-in security features.
Android provides tools and libraries that facilitate encryption processes. Utilizing these resources, developers can encrypt data both in transit (while being transmitted over networks) and at rest (when stored on the device).
One common method is to use the Android’s Keystore system. This is a hardware-backed security feature that securely stores encryption keys.
In case of device compromise, the keys remain safe. Developers use AES encryption to secure sensitive data.
Authenticate Your App
Authentication through Comodo Code Signing Certificate instills confidence in users. It assures them that they’re downloading a legitimate application.
Code signing involves digitally signing the app to verify the authorship and guarantee that the code remains unaltered. To implement code signing, you can utilize Android Studio’s built-in signing capabilities or opt for a reputable third-party tool.
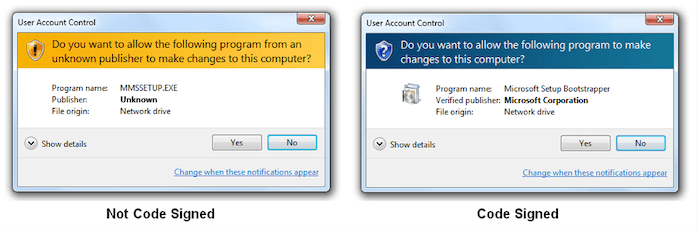
It’s imperative to safeguard your signing keys and refrain from sharing them with unauthorized parties. Here are the key benefits of using code-signing certificates;
- Trust: Code signing establishes trust with users, as it verifies the software’s authenticity. This trust encourages users to download and install the app, knowing it comes from a reliable source.
- Integrity: Code signing ensures that the software hasn’t been tampered with since its last signing. Users can be confident that the app is secure and free from any malicious alterations or code.
- Non-Repudiation: Using code signing certificates on your apps also provides irrefutable evidence of the software’s origins. This means the author cannot deny responsibility, which is crucial in potential disputes or legal proceedings.
Securing App Code and Resources

Securing app code and resources is paramount in Android app development. This Android app security practice could just be what you need to shield your application from potential threats.
Tools like ProGuard and R8 play a key role by obfuscating the code, essentially scrambling it, making it complex for malicious actors to decipher or manipulate. Implementing this involves four easy steps;
- Code Obfuscation: Use tools like ProGuard or R8. They transform your application’s binary file into a cryptic form, making it difficult to interpret or alter.
- Access Control: Restrict permissions strictly to what’s essential for your application’s functionality. Avoid unnecessary access, minimizing potential vulnerabilities.
- Library Security: Ensure that the libraries used in your application are current and secure. Outdated libraries may have known vulnerabilities that could be exploited.
- Secure Coding Practices: Regularly review and update your coding techniques to align with industry best practices. This ensures that you’re employing the most robust security measures available.
Built-in Security Features
Employing built-in security features is another key Android app security best practice to adhere to. These features, including Play Protect, Safe Browsing, and protection from suspicious messages, can significantly bolster your app’s security.
Play Protect for example, continuously scans apps for potential security threats. This ongoing malware check ensures that any risks are swiftly identified and neutralized, providing a robust defense against malicious intrusions.
Safe Browsing serves as a crucial barrier against dangerous websites known for harboring harmful content. Since it preemptively blocks access to such sites, it shields your app from potentially damaging web traffic.
What’s more, the protection from suspicious messages adds an extra layer of security, particularly for apps that facilitate text-based communication. This feature can help identify and thwart dubious messages.
This offers pivotal protection against phishing attacks and unwanted spam. To implement these practices, app developers should integrate these features into their apps during the development process. This involves configuring the settings and permissions within the app to leverage the protective capabilities offered by Play Protect, Safe Browsing, and message screening.
Implement Advanced Security Measures
Implementing advanced security measures for Android app permissions is crucial for increased protection against potential threats. Biometric authentication, such as fingerprints or facial recognition, elevates security by relying on unique biological attributes.
This surpasses conventional passwords and presents a formidable challenge for hackers. Hardware-backed keystores provide an added layer of defense by storing encryption keys in the device’s hardware, making them significantly harder to extract compared to software-based methods.
This safeguards sensitive information effectively. You may also want to implement 2FA or Multi-Factor authentication. Integrating Two-Factor Authentication (2FA) mandates users to verify their identity twice before granting access, adding an extra level of security to the app.
Regular updates are equally vital. They ensure that your app is equipped with the latest security patches and protocols. This further reinforces its resilience against emerging threats.
Frequently Asked Questions of Android App Security
Q: How can I check an app’s permissions before installing?
Before installing an app from the Google Play Store, you can scroll down to the "App permissions" section to see which permissions the app requests. With recent Android versions, you can also grant or deny permissions after installation when the app tries to use a specific feature.
Q: Are apps from third-party app stores safe?
While some third-party app stores might have legitimate apps, they may not have as stringent a review process as the Google Play Store. This can increase the risk of downloading malicious or compromised apps. It’s always advisable to stick to well-known and trusted sources for app downloads.
What are the risks associated with rooting my Android device?
Rooting gives users superuser access to the device’s system files. While this offers more control and customization options, it also bypasses built-in security measures. Rooted devices are more susceptible to malware, can become unstable, and may no longer receive official updates.
What’s the difference between app sandboxing in Android
App sandboxing is a security mechanism where each app runs in its isolated user space and cannot access other apps’ data without explicit permissions. This ensures that, even if an app is compromised, the malicious code is restricted to that app’s sandbox and has limited access to the rest of the system.
A Final Note
Remember, never compromise on the security of your app. It may not seem so smooth sailing but implementing the best Android security measures will not only bolster protection.
It will also help enhance user confidence, making for a safer and more reliable user experience. Prioritizing these best practices is a fundamental aspect of responsible app development.