Table of Contents
Password is something we have to pay attension to in a digital world. Our lives are fully intertwined with online platforms, the significance of a robust password cannot be overstated. It’s not just a key to your online accounts; it’s the guardian of your digital identity, personal data, and often your financial security.
However, the need for stronger, impenetrable passwords has never been more critical with cyber threats escalating in sophisticatio. In this article, we’ll embark on a journey through the art and science of creating passwords that not only defy the common hacking strategies but also are manageable for you to remember. From understanding the anatomy of strong passwords to leveraging advanced techniques for maximum security, this step-by-step guide is your ally in fortifying your digital life against the ever-evolving cyber threats.
Understanding Password Vulnerability
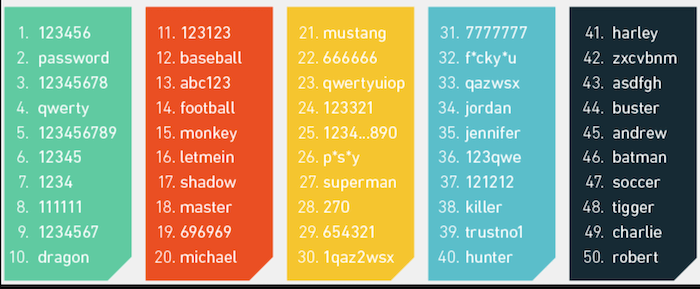
Passwords are often the first line of defense against unauthorized access, and their vulnerability can stem from various factors, such as simplistic or predictable constructions (like using common words or personal information), lack of complexity (absence of a mix of characters, numbers, and symbols), and repetition across multiple platforms. The password that contains pet name kid name could be easily breached according to the research conducted by ExpressVPN.
These vulnerabilities can be exploited through brute force attacks, where hackers use software to try countless combinations, or through more sophisticated methods like phishing and social engineering, where users are tricked into revealing their passwords. Therefore, recognizing these vulnerabilities is the first step towards creating stronger, more resilient passwords that can effectively safeguard digital assets and personal information against potential threats.
Principles of a Robust Password

A robust password typically combines length with complexity, incorporating a mix of upper and lower case letters, numbers, and symbols to create a sequence that is not easily guessable. It should avoid common words, phrases, or easily accessible personal information, as these can be swiftly deciphered by password-cracking tools. Additionally, strong passwords steer clear of predictable patterns, such as sequences or repeated characters, and are unique to each account, preventing a single breach from compromising multiple accounts.
- Length: At least 12 characters. Longer passwords are generally more secure.
- Complexity: Use a mix of uppercase and lowercase letters, numbers, and symbols.
- Unpredictability: Avoid common words, phrases, or obvious substitutions (like "pa$$word").
- No Personal Information: Don’t use easily available information like your name, birthday, or username.
- Avoid Sequential or Repeated Characters: Refrain from using sequences (like "1234") or repeated characters (like "aaaa").
- Different for Each Account: Use a different password for each of your accounts.
- Memorable but Not Obvious: Create a password that you can remember but others can’t easily guess.
- Regular Updates: Change your passwords regularly to mitigate the risk of being compromised.
Adhering to these principles significantly reduces the risk of password-related security breaches, making them an essential aspect of personal and organizational cybersecurity practices.
Step-by-Step Guide to Create a Strong Password
Creating a strong password is a critical step in securing your online presence. Here’s a step-by-step guide to help you craft a password that is both secure and memorable:
Step 1: Start with a Phrase or Sentence
Begin with a phrase or sentence that is meaningful to you but not easily guessed by others. For example, "I love to read books at night!"
Step 2: Use the First Letters of Each Word
Take the first letter of each word in your phrase. Using the example above, this would be "Iltrban".
Step 3: Integrate Numbers and Symbols
Replace some letters with numbers or symbols that resemble them. For instance, replace ‘I’ with ‘1’, or ‘a’ with ‘@’. From the example, "Iltrban" could become "1lt@bn".
Step 4: Add Complexity with Upper and Lowercase
Mix upper and lowercase letters to add complexity. For example, "1lt@bn" can be altered to "1Lt@Bn".
Step 5: Include a Unique Element for Each Site
Customize the password for each site or service. For instance, for your Gmail account, you might add "Gm" at the beginning or end, resulting in "Gm1Lt@Bn" or "1Lt@BnGm".
Step 6: Test Your Password Strength
Use online password strength testers to ensure your password is robust. If it’s weak, add more complexity with additional characters, numbers, or symbols.
Step 7: Remembering Your Password
If you struggle to remember your passwords, consider using a mnemonic device or a password manager. Avoid writing down passwords where they can be easily found.
By following these steps, you can create a password that is difficult for cybercriminals to crack, yet still possible for you to recall. Remember, the key to a strong password is its uniqueness and complexity, making it an effective shield against unauthorized access.
Advanced Strategies for Extra Security: 2FA and Password Manager
Advanced strategies such as Two-Factor Authentication (2FA) and the use of password managers are essential for enhancing online security beyond just having strong passwords. Two-Factor Authentication adds an extra layer of security by requiring a second form of verification in addition to your password. This could be something you know something you have (such as a mobile device that receives a code), or something you are (like a fingerprint or facial recognition). By implementing 2FA, even if a hacker manages to decipher your password, they would still need this second factor to gain access to your account, significantly reducing the risk of unauthorized access.
Password managers are another critical tool in bolstering online security. They help in creating and storing complex, unique passwords for each of your online accounts. These tools generate passwords that are almost impossible to guess and store them in a secure, encrypted vault, accessible only by a master password. This not only alleviates the burden of remembering multiple strong passwords but also ensures that you’re not using the same password across multiple sites, a common practice that can lead to widespread security breaches if one site is compromised.
Furthermore, many password managers offer additional features such as password strength testing, secure sharing of login information, and alerts for when a password needs to be changed or if an account may have been compromised. Some even integrate seamlessly with 2FA, offering a complete package for managing your online security.
By combining the use of a password manager with Two-Factor Authentication, you create a robust defense system for your digital life, significantly reducing the likelihood of cyber attacks and identity theft. It’s a small investment in time and sometimes cost, but the peace of mind and security it brings is invaluable in the increasingly interconnected and digitalized world we live in.
Conclusion
As we conclude this journey through the realms of password security, it’s clear that creating a robust password is less about complex algorithms and more about smart, strategic thinking. The steps outlined in this guide provide a foundation for creating passwords that are not just barriers but formidable fortresses protecting your digital presence.
Remember, your password is your first line of defense in the cyber world. By investing a few moments in creating and regularly updating your passwords, you safeguard not just your personal information but also contribute to the broader landscape of internet security. So, take these lessons, apply them to every account, and move forward with confidence. This makes sure your digital life is secured with passwords that are not just strong, but unbreakable.